MDroid+: Enabling Mutation Testing for Android Apps
Team Members: Mario Linares-Vasquez, Gabriele Bavota, Michele Tufano, Kevin Moran, Christopher Vendome, Massimiliano Di Penta, Carlos Bernal-Cardenas, Denys Poshyvanyk
Purpose
This project was created by the Software Engineering Maintenance and Evolution Research Unit (SEMERU) at the College of William & Mary, in collaboration with Universidad de los Andes, The University of Sannio, and The University of Lugano. The major goal of the MDroid+ project is to help mobile application developers and testers improve the quality of their test suites. This project empirically derived a set of 38 Android-sepcific mutation operators which can be automatically seeded into a target application and analyzed on a set of test cases.
Video Demonstration
Click on the Logo to start the video.
Publications
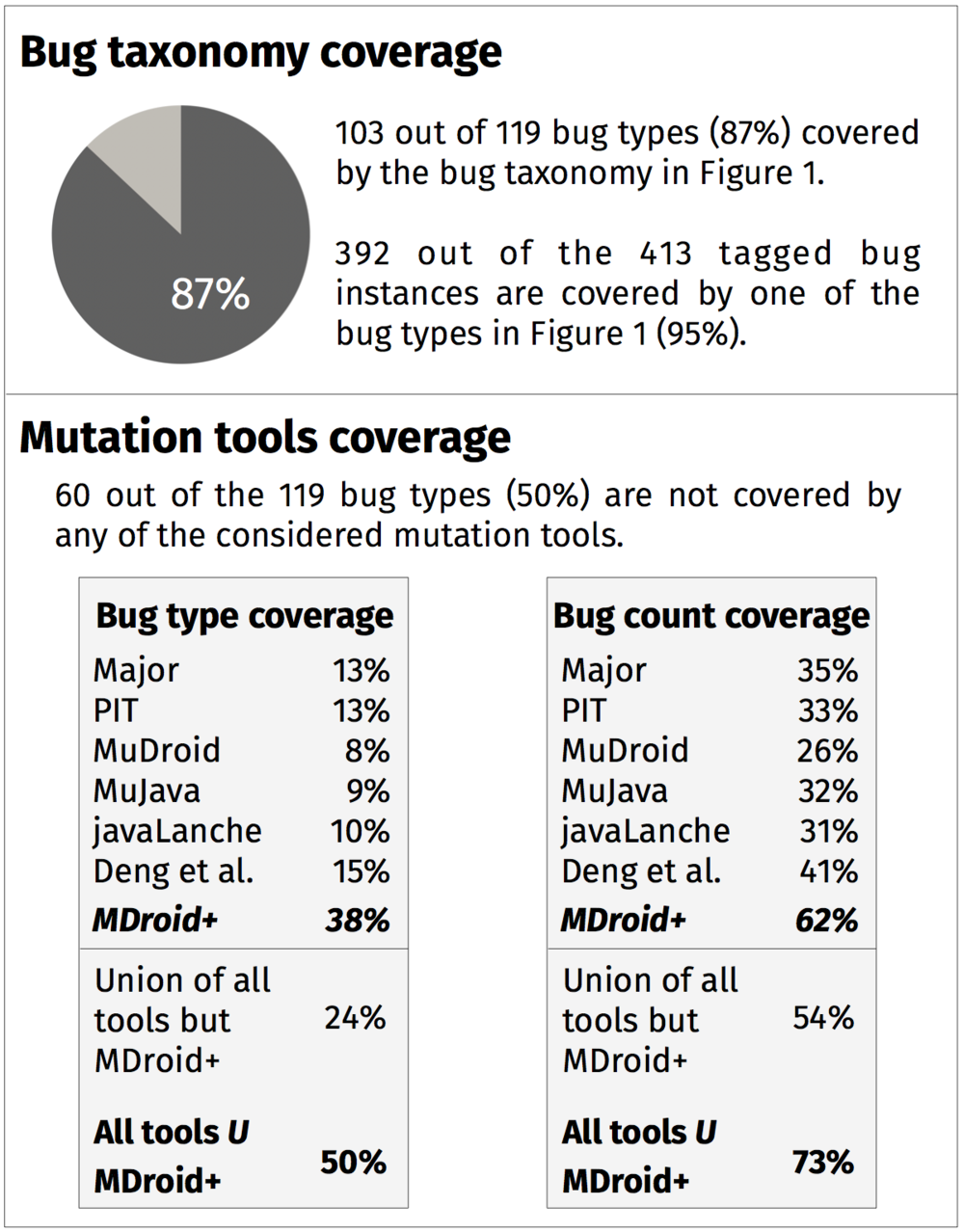
- MDroid+: A Mutation Testing Framework for Android
‣ Kevin Moran, Michele Tufano, Carlos Bernal-Cárdenas, Mario Linares-Vásquez, Gabriele Bavota, Christopher Vendome, Massimiliano DiPenta, and Denys Poshyvanyk
‣ Proceedings of the 40th IEEE/ACM International Conference on Software Engineering (ICSE'18), Formal Research Demonstrations Track, Gothenburg, Sweden, May 27-June 3, 2018, to appear 4 pages (35% Acceptance Rate)
‣ [pdf | software]
- Enabling Mutation Testing for Android Apps
‣ Mario Linares-Vásquez, Gabriele Bavota, Michele Tufano, Kevin Moran, Massimiliano DiPenta, Christopher Vendome, Carlos Bernal-Cárdenas and Denys Poshyvanyk
‣ Proceedings of 11th Joint Meeting of the European Software Engineering Conference and the 25th ACM SIGSOFT Symposium on the Foundations of Software Engineering (ESEC/FSE'17), Paderborn, Germany, September 4-8, 2017, pp. 233-244 (24.4% Acceptance Rate)
‣ [pdf | software]
Table of Contents
- Empirical Study
- Fault Taxonomy
- Mutation Operators
- MDroid+ & Code
- Empirical Evaluation
- Apps Used in Study
- RQ1
- RQ2
- RQ3
- Data